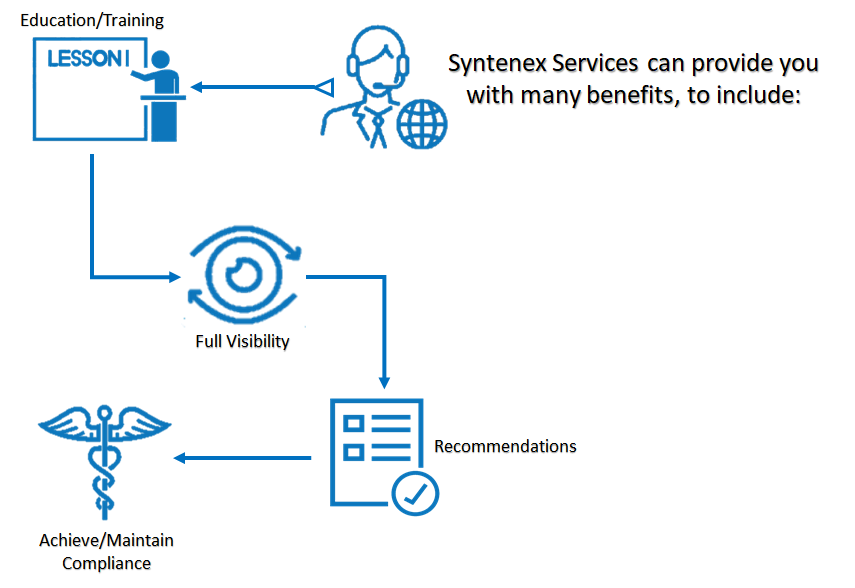
We Manage The Cyber Risk to Protect Your Business
SYNTENEX Corporation Auditors can review and assess your organization's regulatory compliance processes, Risk Exposure, Identify areas of concern, and Recommend the necessary improvements required to successfully satisfy regulatory mandates.
Health Insurance Privacy and Accountability Act (HIPAA)
Payment Card Industry Security Standard (PCI)
Sarbanes Oxley (SOX)
Gramm-Leach-Bliley Act (GLBA)
ISO/IEC 27000 Family of Standards (ISO/IEC 27K)
Federal Information Security Management Act (FISMA)
Cyber Threats
Brand and Data Exposure
Infrastructure and Physical Exposure
Health Insurance Privacy and Accountability Act (HIPAA)
Effective February of 2010, the Health Insurance Portability and Accountability Act of 1996 (HIPAA) was modified, as required by the Health Information Technology for Economic and Clinical Health (HITECH) Act signed into law in 2009. The modifications require HIPAA covered entities (health care providers, health plans, or health care clearinghouses) to notify the Department of Health and Human Services (HHS) in the event of a breach of records in excess of 500. In addition, all those business associates that their daily operations involve the use or disclosure of protected health information on behalf of or provide services to a covered entity now must comply with HIPAA and are directly regulated by HHS.
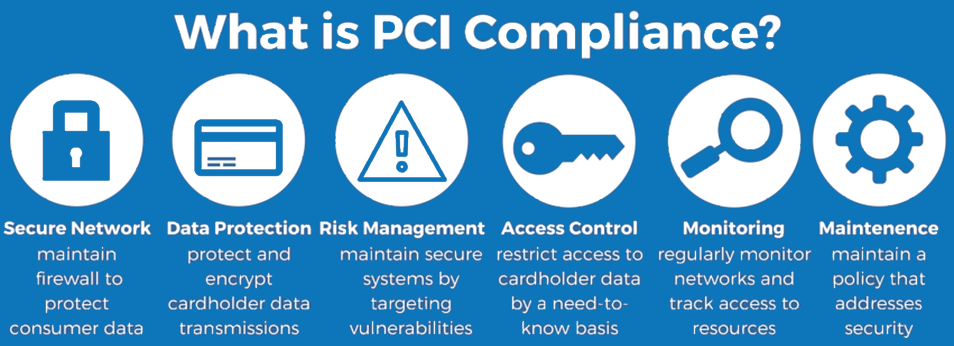
Payment Card Industry Security Standard (PCI)
If your organization stores or processes credit cards payments, then you must comply with the PCI Data Security Standards developed by the PCI Security Standards Council. The Council was formed by American Express, Visa, Discover and JCB Master Card. The Council developed the PCI Data Security Standard, in which all payment card merchants and service providers will be held accountable.
Syntenex can help your organization achieve PCI Compliance at a minimal cost.
Sarbanes Oxley (SOX)
This legislation was enacted to protect shareholders and the general public from accounting errors and fraudulent practices in the enterprise. The Securities and Exchange Commission (SEC) sets deadlines for compliance and publishes rules on requirements. To be SOX compliant, you MUST store all records required by the Act for corporations in the financial field as well as the IT Departments whose job it is to store a corporation’s electronic records.
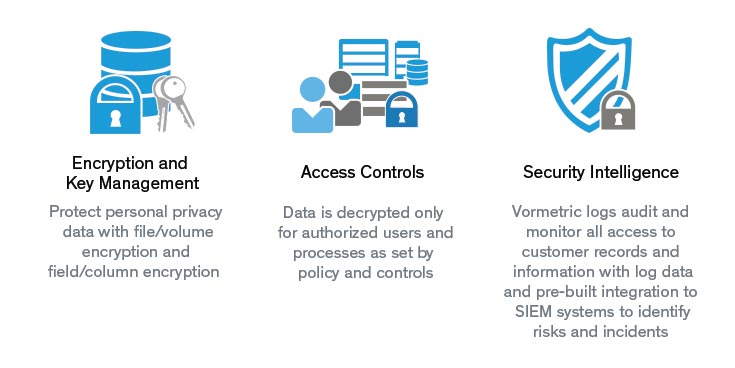
Gramm-Leach-Bliley Act (GLBA)
Protecting the privacy of consumer information held by “financial institutions” is at the heart of the financial privacy provisions of the Gramm-Leach-Bliley Financial Modernization Act of 1999. The GLB Act requires companies to give consumers privacy notices that explain the institutions’ information-sharing practices. In turn, consumers have the right to limit some – but not all – sharing of their information.
ISO/IEC 27000 Family of Standards (ISO/IEC 27K)
The ISO / IEC 27000 family is a series of information security standards developed and published by the International Standards Organization (ISO) and the International Electrotechnical Commission (IEC). These standards provide a globally recognized framework for best practice information security management.
Why use it?
It should be noted that Specification Number 27001 lists specific requirements, all of which must be followed. These standards are applicable to any organization, in any sector, of any size.
Why Syntenex?
Information security is an issue of paramount importance to all organizations. With the exponential development of technology, it is imperative that organizations protect their own assets, whilst also ensuring confidence in the clients, customers, and partners they work with. Syntenex can help your organization to comply with ISO 27001 by:
- Assisting with the proper security for all critical assets
- Managing levels of risks
- Evolving your information security alongside technological developments.

Federal Information Security Management Act (FISMA)
Most internal IT organizations continue to struggle with attaining and maintaining FISMA compliance across all IT systems as the cost, complexity, and associated risks of IT security continue to accelerate.
FISMA assigns specific responsibilities to federal agencies, the National Institute of Standards and Technology, as well as the Office of Management Budget to strengthen information system security.
Good Business Reputation isn’t something that can be earned by accident – Let us Manage Your Risk
Cyber Threats
Brand and Data Exposure
Infrastructure & Physical Exposure



